Crackin dat Hash
So...let's step outside of the challenge for a bit. In any normal engagement, I would attempt to send my newly found hash to a dedicated cracking rig (preferably one that isn't in the cloud as this is basically company-specific sensitive data that should never leave the hands of the ethical penetration tester) and try this hash against some of the more known password cracking lists that many have, such as the latest RockYou2021.txt wordlist. But thinking back, the source code of the registration page had some interesting words.
It became fairly obvious that the next step here is to build our own wordlist. And I can do that using CeWL!
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 | |
Good times. I have a feeling this won't work, but let's try cracking the hash with this wordlist.
First, we'll need to find the mode for hashcat to work with. To do that, I can dump the example hashes, or I can just visit the site:
And search for the beginning of the hash:
$krb5tgs$23$
So I'll search for krb5tgs with a Ctrl+F...
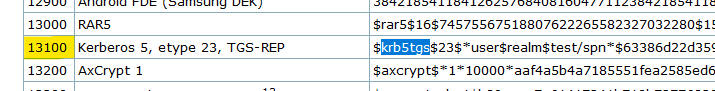
And we have a match! Mode 13100!
So attempting with what little I currently have...
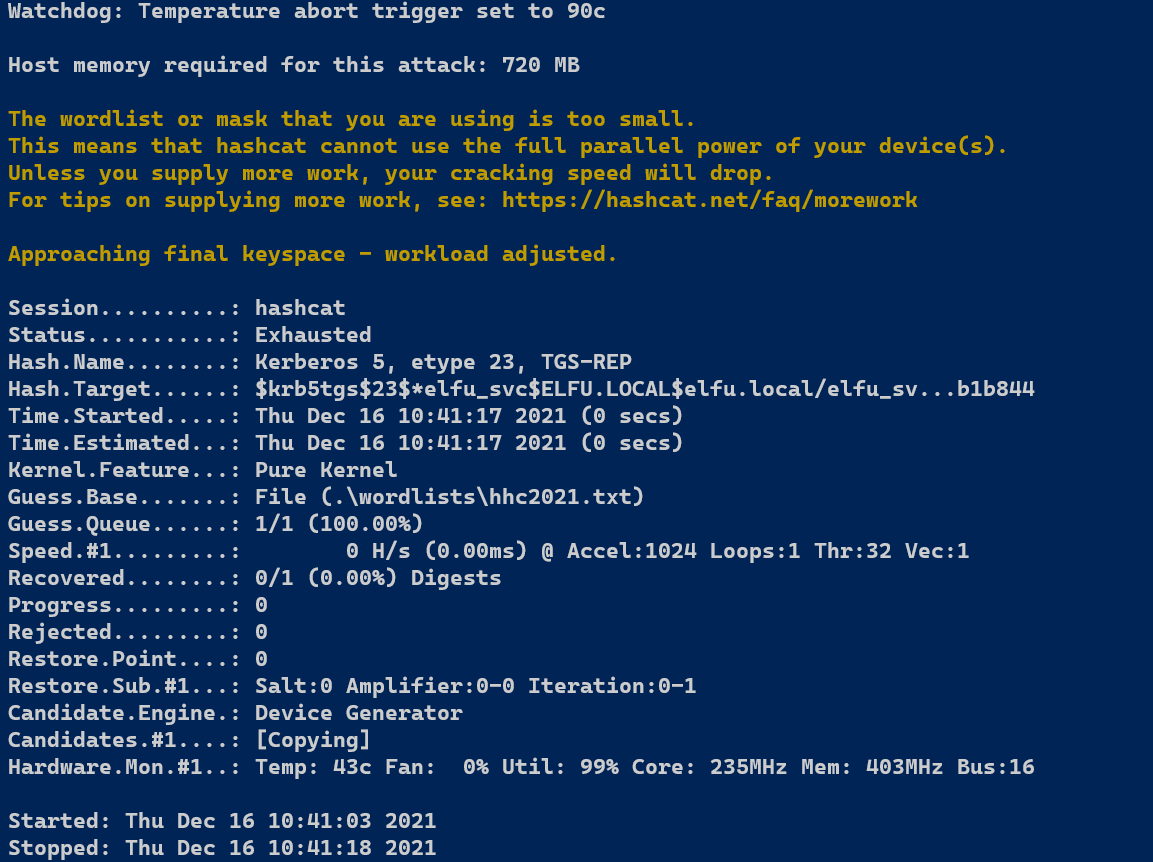
Oh well. Let's massage the wordlist a bit!
Using the "One Rule To Rule Them All" ruleset...
Instead of creating a new wordlist, I am just going to apply a password ruleset with my wordlist that I created from the above.
.\hashcat.exe -m 13100 -a 0 .\hashes\hhc2021.txt --potfile-disable -r .\rules\oneruletorulethemall.rule --force -O -w 4 --opencl-device-types 2 .\wordlists\hhc2021.txt
aaaaand...
Cracked!
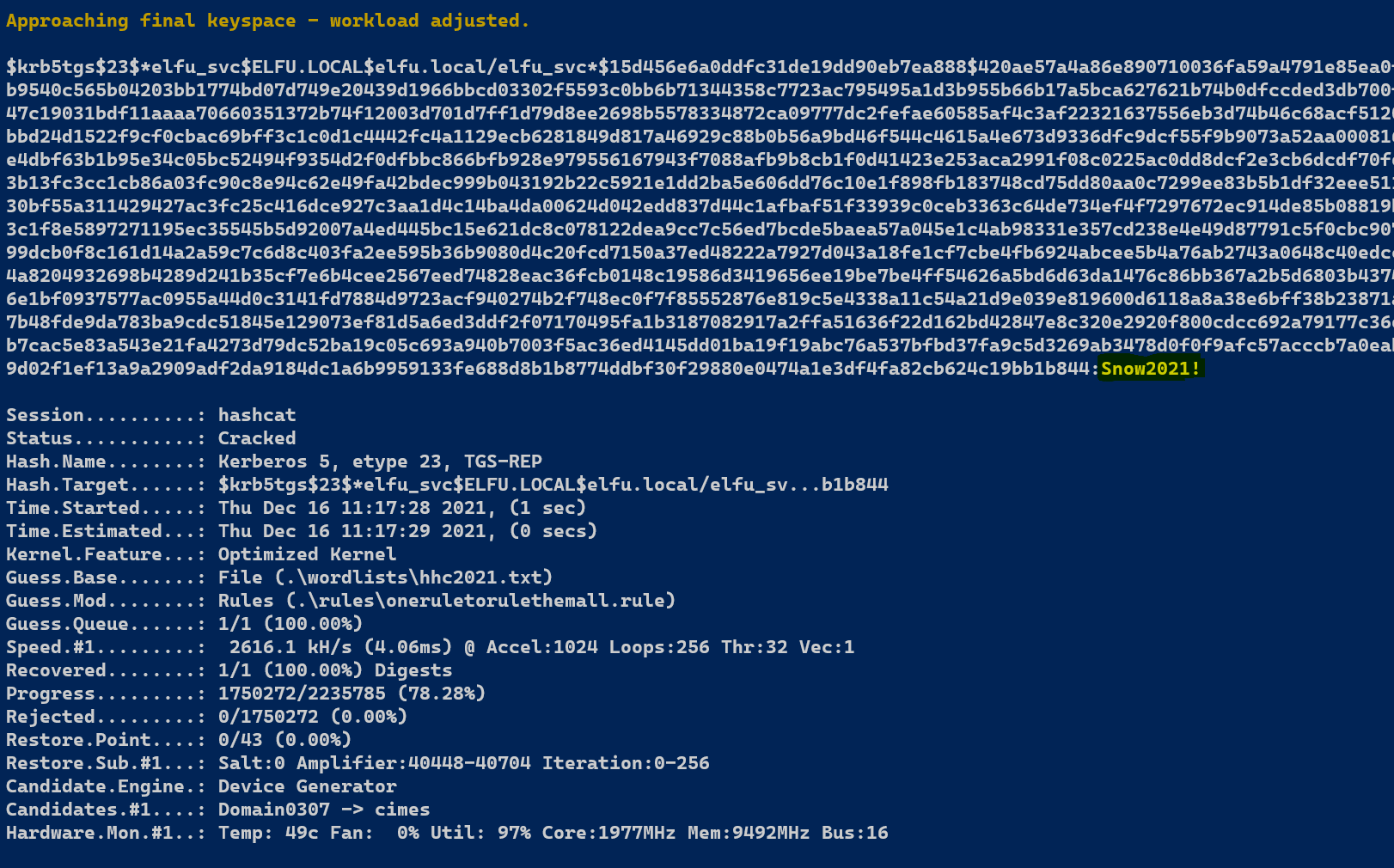
Password is Snow2021!